by valino | Feb 23, 2026 | Network
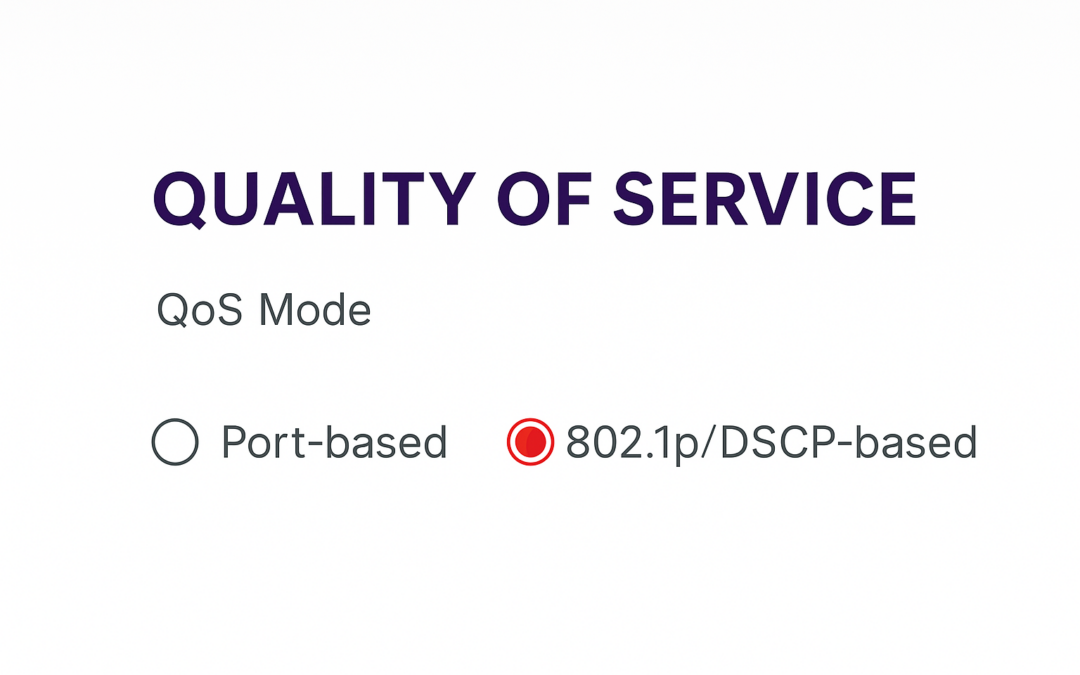
Port-Based QoS vs 802.1p/DSCP QoS: What’s the Difference? If you’re new to networking, you’ve probably seen QoS settings like Port-based QoS and 802.1p/DSCP-based QoS on your router or switch. But what do these terms actually mean? And which one should you use? This...
by valino | Dec 18, 2025 | Uncategorized
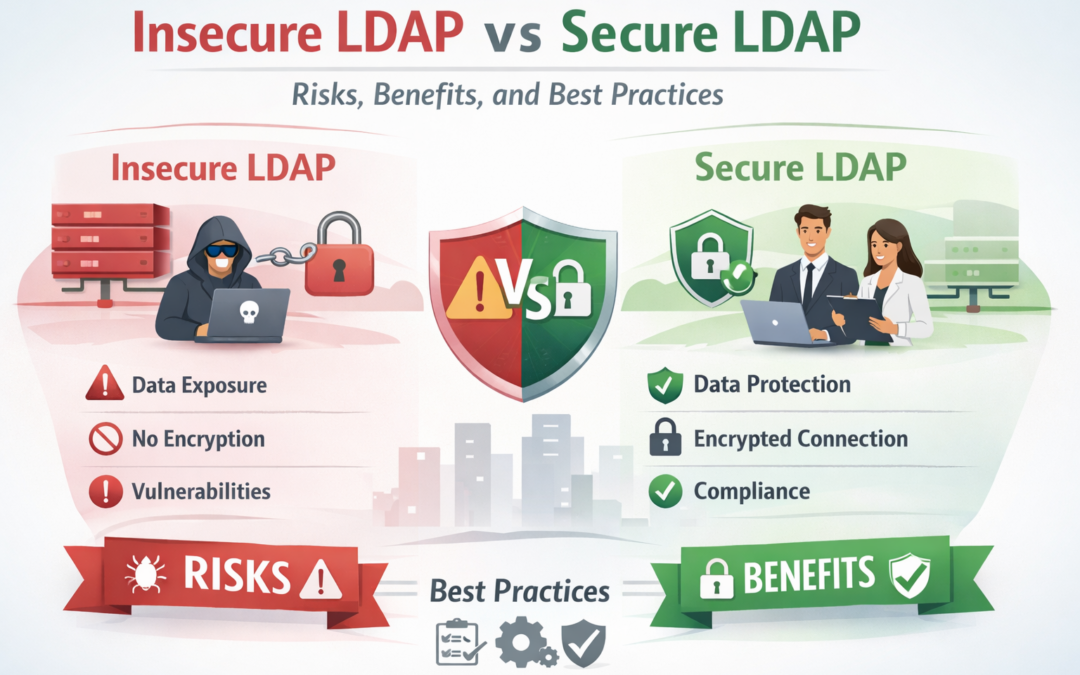
LDAP plays a critical role in enterprise identity management, but when deployed insecurely, it becomes a major cybersecurity liability. With over 30 years of cybersecurity experience, this guide explains the difference between Insecure LDAP and Secure LDAP (LDAPS),...

by valino | May 27, 2025 | Network, Hacking
The Domain Name System (DNS) is a critical component of the internet’s infrastructure, but it’s also a frequent target for cybercriminals. A DNS attack exploits vulnerabilities in DNS protocols or configurations to redirect users, exfiltrate data, or disrupt...
by valino | Apr 11, 2025 | Phishing
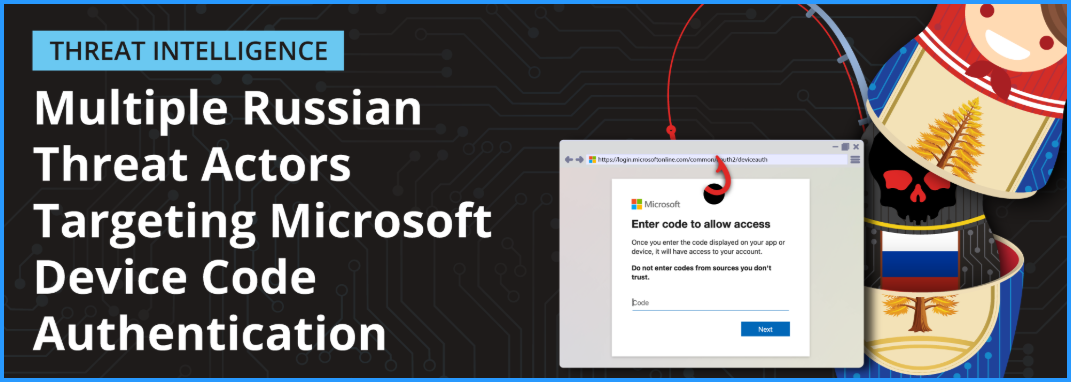
KEY TAKEAWAYS Volexity has observed multiple Russian threat actors conducting social-engineering and spear-phishing campaigns targeting organizations with the ultimate goal of compromising Microsoft 365 accounts via Device Code Authentication phishing. Device Code...

by valino | Apr 4, 2025 | Zero-Day
As cyber threats become increasingly sophisticated, traditional perimeter-based security models are no longer enough. Zero Trust Security has emerged as a modern cybersecurity framework built on the principle of “never trust, always verify.” It assumes...






