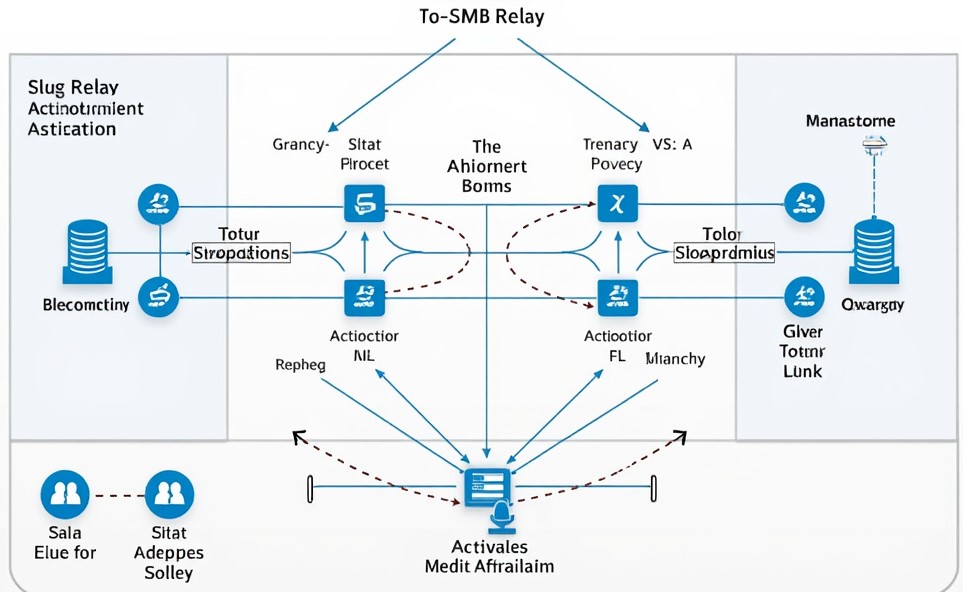
by valino | Aug 29, 2024 | Active Directory
0. Overview Many organizational networks rely on Active Directory (AD) to streamline administrative tasks and enhance efficiency. However, in its default configuration, AD introduces “features” that attackers could exploit. The SMB (Server Message Block) protocols...

by valino | Jun 10, 2024 | pentesting
Introduction Penetration testing, or “pentesting,” is an essential component of a robust cybersecurity strategy. It involves simulating cyberattacks to identify vulnerabilities in a system before malicious actors can exploit them. While system...

by valino | May 14, 2024 | pentesting
Technology evolves for both the good and bad. Tech gurus create new software and systems to make processes more accessible, efficient, and precise; while on the other hand, hackers evolve their techniques to exploit IT infrastructure weaknesses. That’s why companies...

by valino | Feb 27, 2024 | Web App Pentesting
Race conditions in the realm of cyber security are critical vulnerabilities that can lead to unpredictable outcomes, potentially compromising the security of software systems. This post is designed to demystify this complex concept, breaking it down into easily...

by valino | Feb 13, 2024 | Compliance
Introduction to GDPR The General Data Protection Regulation (GDPR) stands as a monumental piece of legislation within the European Union, aimed at strengthening and unifying data protection for all individuals. Its introduction marked a significant shift in the data...






