by valino | Dec 2, 2023 | Hacking, SOC
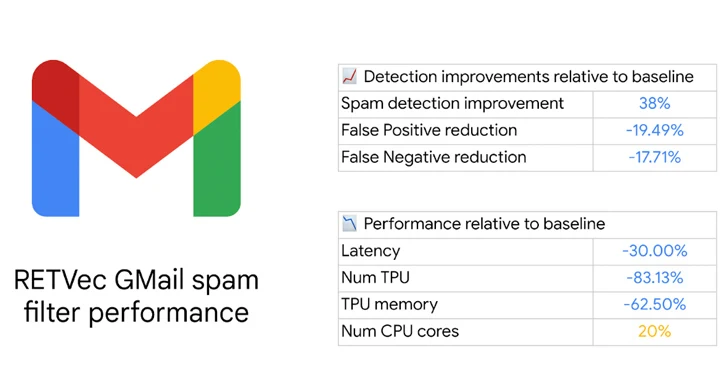
Google has revealed a new multilingual text vectorizer called RETVec (short for Resilient and Efficient Text Vectorizer) to help detect potentially harmful content such as spam and malicious emails in Gmail. “RETVec is trained to be resilient against...

by valino | Dec 2, 2023 | Zero-Day
A suspected Chinese-speaking threat actor has been attributed to a malicious campaign that targets the Uzbekistan Ministry of Foreign Affairs and South Korean users with a remote access trojan called SugarGh0st RAT. The activity, which commenced no later than August...

by valino | Dec 2, 2023 | Zero-Day
Apple has released software updates for iOS, iPadOS, macOS, and Safari web browser to address two security flaws that it said have come under active exploitation in the wild on older versions of its software. The vulnerabilities, both of which reside in the WebKit web...

by valino | Nov 18, 2023 | SOC
In the complex world of cybersecurity, understanding how attackers operate is crucial for robust defense strategies. Attack frameworks, systematic representations of the tactics, techniques, and procedures (TTPs) used by cyber adversaries, are indispensable tools in...

by valino | Nov 11, 2023 | Network
In the vast universe of cybersecurity, there exists a sentinel known as a reverse proxy, which stands guard between your web server and the relentless sea of internet traffic. Acting as an intermediary, the reverse proxy evaluates requests coming from the internet...






