Blog Posts & Articles
Cybersecurity Updates, Recent Vulnerabilities, and Hacking Guides.
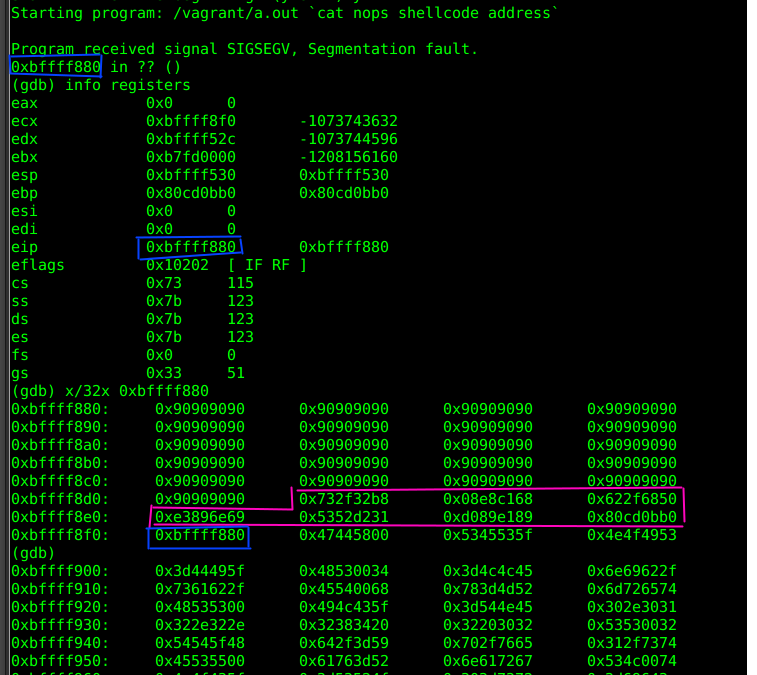
Buffer Overflow Vulnerabilities: Understanding and Mitigating the Risk Introduction In the realm of cybersecurity, buffer overflow vulnerabilities have long been a prevalent issue. These weaknesses can lead to severe consequences, including unauthorized access to...

DNS Attacks: How to Detect and Secure Your Network from DNS Threats
The Domain Name System (DNS) is a critical component of the internet's infrastructure, but it’s also a frequent target for cybercriminals. A DNS attack exploits vulnerabilities in DNS protocols or configurations to redirect users, exfiltrate data, or disrupt services....
No Results Found
The page you requested could not be found. Try refining your search, or use the navigation above to locate the post.
Stay Secure with the Latest Cyber Security News and Trends
Threat Landscape
IoT Security
Social Engineering
Zero Trust
Incident Response
Cloud Safety
Know the Latest on Cyber Security
Insecure LDAP vs Secure LDAP: Risks, Benefits, and Best Practices
LDAP plays a critical role in enterprise identity management, but when deployed insecurely, it becomes a major cybersecurity liability. With over 30 years of cybersecurity experience, this guide explains the difference between Insecure LDAP and Secure LDAP (LDAPS),...
DNS Attacks: How to Detect and Secure Your Network from DNS Threats
The Domain Name System (DNS) is a critical component of the internet's infrastructure, but it’s also a frequent target for cybercriminals. A DNS attack exploits vulnerabilities in DNS protocols or configurations to redirect users, exfiltrate data, or disrupt services....
Multiple Russian Threat Actors Targeting Microsoft Device Code Authentication
KEY TAKEAWAYS Volexity has observed multiple Russian threat actors conducting social-engineering and spear-phishing campaigns targeting organizations with the ultimate goal of compromising Microsoft 365 accounts via Device Code Authentication phishing. Device Code...
What Is Zero Trust Security? A Modern Cyber Defense Strategy Explained
As cyber threats become increasingly sophisticated, traditional perimeter-based security models are no longer enough. Zero Trust Security has emerged as a modern cybersecurity framework built on the principle of "never trust, always verify." It assumes that threats...

All Categories
Red Teaming
Blue Teaming
Pentesting
Endpoint Security
Network Defense
Identity and Access Management
Cryptography
Compliance and Regulations
Secure Coding
Physical Security
Threat Intelligence
Malware Analysis
Stay Up to Date With The Latest News & Updates
Access Premium Content
Unlock a treasure trove of expert cybersecurity insights, in-depth analyses, and exclusive reports. Go premium and stay ahead of the digital threats with our top-tier content
Join Our Newsletter
Stay informed and vigilant. Subscribe to our newsletter for the latest in cybersecurity trends, threats, and best practices—delivered straight to your inbox
Follow Us
Dive deeper into the world of cybersecurity. Follow us on our social channels for daily insights, tips, and exclusive content