Understanding the SOAR Paradigm
Security Orchestration, Automation, and Response (SOAR) is a synergistic suite of software applications tailored for enhancing an organization’s capability to promptly gather threat intelligence and respond autonomously to security incidents.
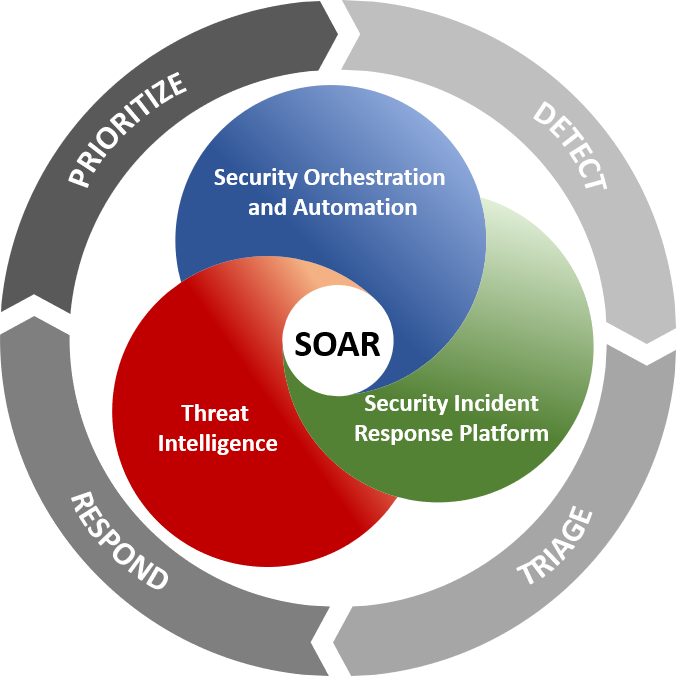
Three Pillars of SOAR
- Security Orchestration: It acts as a unifier, knitting together various security tools and solutions, both internal and external, via predefined or custom integrations and APIs. This orchestrated approach offers a holistic view, combining insights from firewalls, intrusion detection systems, vulnerability assessment tools, and more.
- Security Automation: By leveraging the immense data flow from orchestration, SOAR platforms employ AI and machine learning to automate routine tasks, such as log assessments and vulnerability scans. This not only streamlines operations but also fosters a dynamic response mechanism.
- Security Response: This provides a consolidated perspective for analysts to manage, monitor, and report on actions undertaken post-threat detection. It encapsulates activities from threat intelligence sharing to post-incident reporting.
SOAR: A Boon for Small and Medium Businesses
SOAR platforms revolutionize security operations for businesses, especially SMBs. Their benefits span from reduced detection and response times to streamlining operations. Key advantages include:
- Rapid Threat Detection: With enriched data context and automation, SOAR diminishes the mean time to detect and respond, minimizing potential damage.
- Enhanced Threat Intelligence: By harmonizing data across tools, SOAR delivers enriched analysis and real-time threat updates.
- Unified Management Interface: SOAR amalgamates various security dashboards, simplifying data management and operations.
- Scalability: As security events proliferate, manually scaling operations becomes unfeasible. SOAR meets these demands gracefully with automation.
- Boosted Productivity: By automating menial tasks, SOC teams can prioritize effectively, ensuring timely responses.
- Operational Efficiency: Standardized playbooks ensure consistent, organization-wide remediation strategies.
- Collaborative Reporting: Consolidated data analysis and a unified dashboard foster enhanced cross-team communication and data-sharing.
- Cost Efficiency: Integrating SOAR tools can significantly reduce operational costs compared to manual threat management.
Additional Security Insights
While SOAR is transformative, it’s not a panacea. For holistic security, integrating SOAR within a layered defense strategy is imperative. Other essential steps include adopting two-factor authentication, password managers, robust password policies, and regular risk assessments. For a comprehensive defense strategy, explore CyberHoot’s recommendations.