Introduction to Kerberos
Understanding the Basics of Kerberos
Kerberos, named after the mythical Greek guardian of the underworld, is a robust network authentication protocol designed to provide strong authentication for client-server applications. Developed at the Massachusetts Institute of Technology (MIT), Kerberos uses secret-key cryptography to ensure secure communication over non-secure networks, primarily in a client-server model. It has become an integral component of contemporary cybersecurity strategies, safeguarding sensitive data and transactions in various environments.
The Significance of Kerberos in Network Security
In today’s digital age, where data breaches and cyber threats are rampant, Kerberos plays a crucial role in fortifying network security. Its ability to authenticate users without transmitting passwords over the network makes it a preferred choice for organizations seeking to enhance their security posture. Kerberos is widely adopted in various sectors, including finance, healthcare, and government, for its robust security features and reliability.
Historical Background of Kerberos
Development and Evolution of Kerberos
Kerberos was developed in the 1980s as part of MIT’s Project Athena. The objective was to create a secure, reliable authentication system for the project’s distributed computing environment. Over the years, Kerberos has evolved, with several versions being released. Each iteration has brought enhancements and new features, addressing the evolving security needs of modern networks.
Key Milestones in Kerberos’s History
The journey of Kerberos is marked by significant milestones. Starting with Version 4, which laid the foundation for modern Kerberos, to the widely used Version 5, each version has contributed to its standing as a highly secure and
efficient authentication protocol. The adoption of Kerberos by major platforms like Microsoft Windows and its incorporation into various enterprise-level solutions further testify to its significance in the realm of network security.
How Kerberos Works
The Kerberos Authentication Process
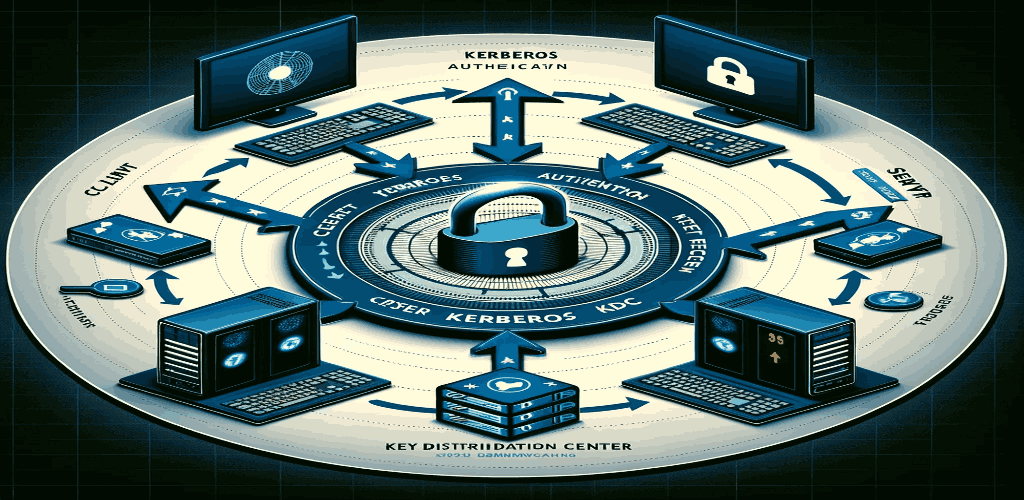
Kerberos operates on a simple yet effective principle: it allows nodes communicating over a non-secure network to prove their identity to one another in a secure manner. This process involves three primary entities: the client, the Key Distribution Center (KDC), and the server. The KDC, central to the Kerberos architecture, consists of two parts – the Authentication Server (AS) and the Ticket Granting Server (TGS).
The authentication process typically involves the client requesting an authentication ticket from the AS, using this ticket to obtain a service ticket from the TGS, and finally presenting this service ticket to the server to access the desired service.
Key Components and Their Functions
Each component in the Kerberos protocol plays a pivotal role:
- Authentication Server (AS): Validates the identity of the client and issues a TGT (Ticket Granting Ticket).
- Ticket Granting Server (TGS): Issues service tickets based on the client’s TGT, allowing access to various services.
- Client: Initiates the authentication process and communicates with both the AS and TGS to obtain the necessary tickets.
- Server: Hosts the services that the client wants to access, relying on Kerberos for secure authentication of clients.
The Kerberos Protocol
Detailed Analysis of the Kerberos Protocol
The Kerberos protocol is a masterclass in balancing security and efficiency. It uses symmetric key cryptography, where the same key is used for both encryption and decryption. This approach, coupled with the use of tickets and timestamps, ensures that the authentication process is both secure and streamlined.
Ticket-Granting System and Service Tickets
A standout feature of Kerberos is its ticket-granting system. Once authenticated, the client receives a TGT, which it can use to obtain service tickets for various network services without having to re-authenticate each time. This not only enhances security by minimizing password transmission but also improves user experience by reducing authentication steps.
Security Features of Kerberos
Encryption Techniques Used in Kerberos
Kerberos employs advanced encryption techniques to secure communications between the client and the server. The use of secret-key cryptography ensures that the information exchanged during the authentication process remains confidential and tamper-proof.
Preventing Unauthorized Access and Attacks
Kerberos is designed to thwart a range of cyber threats, including replay attacks, eavesdropping, and impersonation. The protocol’s reliance on timestamps and session keys plays a crucial role in mitigating these threats, providing a robust defense mechanism against unauthorized access.
This article will continue to delve into the implementation, comparison with other systems, troubleshooting, and the future trajectory of Kerberos. It will also provide insights into real-world applications, compliance aspects, and resources for learning more about this essential protocol.