by valino | Jan 14, 2024 | Network
Introduction to Kerberos Understanding the Basics of Kerberos Kerberos, named after the mythical Greek guardian of the underworld, is a robust network authentication protocol designed to provide strong authentication for client-server applications. Developed at the...
by valino | Jan 14, 2024 | Network
Introduction to RADIUS Overview of RADIUS Protocol RADIUS, short for Remote Authentication Dial-In User Service, is a networking protocol that provides centralized Authentication, Authorization, and Accounting (AAA) management for users who connect and use a network...

by valino | Jan 11, 2024 | Network
Introduction to the OSI Model Understanding the OSI Model Concept The OSI (Open Systems Interconnection) Model is a conceptual framework used to understand network architecture and the various processes involved in the transfer of data. Developed by the International...
by valino | Jan 9, 2024 | Network
Network Address Translation (NAT) is a crucial component in enhancing the security and efficiency of network communication, especially for devices connected to the internet through a firewall. In this article, we explore why applying NAT to an internet-facing firewall...

by valino | Jan 9, 2024 | Network
To prevent broadcast storms, which can severely disrupt network performance, a combination of network design strategies, hardware configurations, and proactive monitoring practices should be employed. Here’s a detailed approach: Understanding Broadcast Storms A...

by valino | Jan 5, 2024 | Network
The Domain Name System (DNS) is often likened to the phonebook of the internet, translating human-friendly domain names into IP addresses that computers use. However, the traditional DNS has vulnerabilities that can be exploited to redirect users to malicious sites....

by valino | Dec 16, 2023 | Hacking
Multiple security vulnerabilities have been discovered in the open-source Netgate pfSense firewall solution called pfSense that could be chained by an attacker to execute arbitrary commands on susceptible appliances. The issues relate to two reflected cross-site...

by valino | Dec 16, 2023 | Hacking
A previously unknown hacker outfit called GambleForce has been attributed to a series of SQL injection attacks against companies primarily in the Asia-Pacific (APAC) region since at least September 2023. “GambleForce uses a set of basic yet very effective...
by valino | Dec 2, 2023 | Hacking, SOC
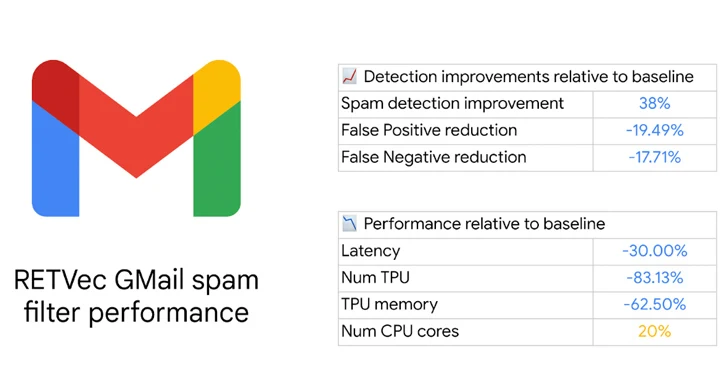
Google has revealed a new multilingual text vectorizer called RETVec (short for Resilient and Efficient Text Vectorizer) to help detect potentially harmful content such as spam and malicious emails in Gmail. “RETVec is trained to be resilient against...

by valino | Dec 2, 2023 | Zero-Day
A suspected Chinese-speaking threat actor has been attributed to a malicious campaign that targets the Uzbekistan Ministry of Foreign Affairs and South Korean users with a remote access trojan called SugarGh0st RAT. The activity, which commenced no later than August...











